Spotting a phish
Phishing is the most popular form of cyber crime. It’s a scam form that has been around for years from the comical prince to the current COVID-19 disguise.
The very best have fallen victim to phishing scams. For example, the recent Twitter hack started as a cleverly engineered spear-phishing scam.
These ultra-engineered targeted phishing scams use specifically farmed information to intercept and build trust.
However, there are still many low value mass released phishing scams that we need to watch out for, a lapse in judgement, and one wrong click, could lead to malware, viruses, and access to key personal information for the criminals.
All email accounts have some level of spam filtering whether this is your work account or your personal account. These are automated systems, clever, but not full proof.
The next line of defence is you! This is where this article is here to help. There are cues that if we identify, will allow us to quickly determine if the email is genuine or not.
What’s the @ address?
Legitimate organisations will generally send you an email from there domain name and not from ‘@gmail.com’ or ‘@hotmail.co.uk’.
For instance, our domain name is select-technology.co.uk, therefore our emails are sent from personname@select-technology.co.uk.
Job done! Unfortunately, no, the criminals are far cleverer then that.
Often when you are sent an email you are shown the sender name, this can be selected by the criminal. Look at the actual email address, what does that say?
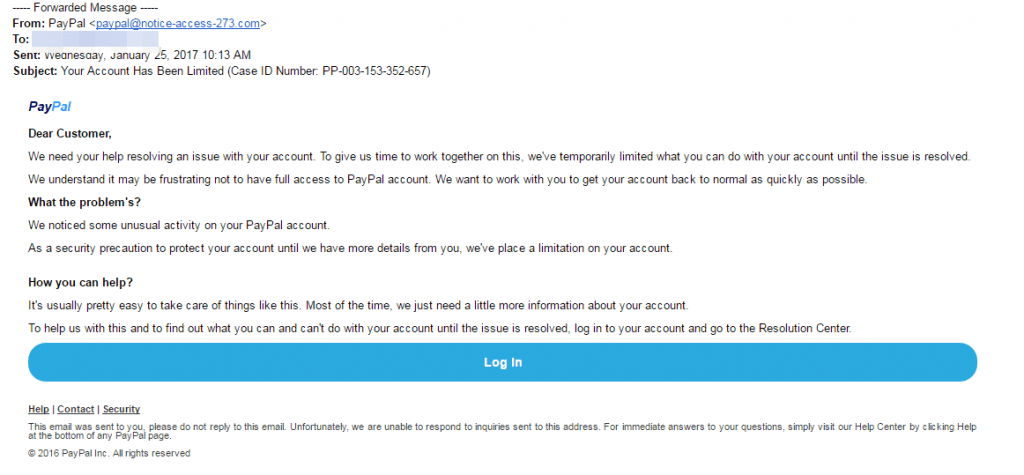
Even here be on your guard!

Can you notice anything ‘phishy’ about the above, everything seems above board? The red flag is the email came from ‘@notice-access.co.uk’. The fact that it has the name and part of the domain name in the email address might be enough to fool some, so its important to really interrogate the sender address.
Another variation on the @ address is to misspell, but only ever so slightly. Maybe @select-technology.co.uk becomes @seiect-technology.co.uk. A first glance it looks the same, but carefully look at each letter and an ‘l’ has become an ‘i’. Simple but effective.
How well is the email written?
A cursory glance at how well the email is written will tell you if the email is a scam or not.
There is a theory that a poorly written email has been purposely created to target the most gullible people, who ignore these obvious clues. This is only really applicable where the target will directly respond to the criminal, such as prince scam.
Most emails are automated and sent out in bulk. So why the poor spelling and grammar? Often these are sent from individuals where English is there second language and there may be a reliance on spellchecker and translation systems. Both will not take into account the nuances and context that we learn over time.
The fun part is that not all spelling ‘errros’ are made by criminals! It is really easy to mash the wrong letter on the keyboard in a rush or place a comma in the wrong place,
So, when we look at the email we need to ask ourselves does the mistake look normal, does the sentence make sense, does the email feel like a template and does the message feel consistent with the language the sender normally uses. For instance, I sometimes overuse ‘additionally’, are they there or does the author use different words.
Furthermore, if you are in doubt look at all the cues together and if they feel suspicious contact the sender directly via an alternative channel – phone, Teams etc.
Does it have attachments?
Often criminals will send the email with an attachment. These look innocent by are laced with malware or viruses. Once you open them then the damage is likely to have been done.
Look at the previous cues and is this email from a trusted sender. If you have any doubts, then DO NOT click on that attachment or forward it to anyone. Get in touch with the sender directly, don’t use the reply button. Or contact your IT support team, they would much rather have a look at it, and take the right actions, then try and repair the potential damage.
Are you being asked to click on link?
Another way that criminals try to grab information is by ask you to click a link and direct you to what seems like an innocent page. These are quite clever, they may ask you to verify a payment on your amazon account, or your Netflix account is going to expire. Click on this link to continue or view more information.
These emails are often very well presented, but always look for the cues. If you are using a computer hover over the link, what is the destination URL? If it was an email from Netflix you would expect it to start with netflix.com or netflix.co.uk. Scammers hide the links using buttons or alternate text.
The link above, you would expect to go to our services page, but it’s very simple to write one thing, but do something different.
Its urgent!
Criminals use urgency to make us forget to do the checks. Take a moment and do the checks regardless of what the message might imply.
These are extremely effective in the workplace. An email from the Managing Director to saying a payment is late and needs to be actioned immediately. Are you going to question the email? Fear in this instance will make us act against our intuition. Again, contacting the boss or the senior leader to verify via another channel, this is only you protecting the business and its money!
I got an email and I think its real?
Checklist time:
- The @ address looks right.
- The message makes sense.
- The spelling and grammar are correct.
- The links look like they go to where you would expect.
Good to go right?
Wait a second are they asking you to check an invoice or add payment information? – then check with the sender directly and verify that they sent it.
If the email is from an organisation asking you login to an account, don’t use the email. Go directly to the site and login, often these accounts will have all the messages that they have sent to you within the account or if an action is required will let you know once you login.
Make both these actions part of your natural habit and you will have protected both yourself and the organisation that you work for.
I am still not sure, and I could do with some support?
Firstly, its ok to be unsure! You should not be embarrassed to ask for help.
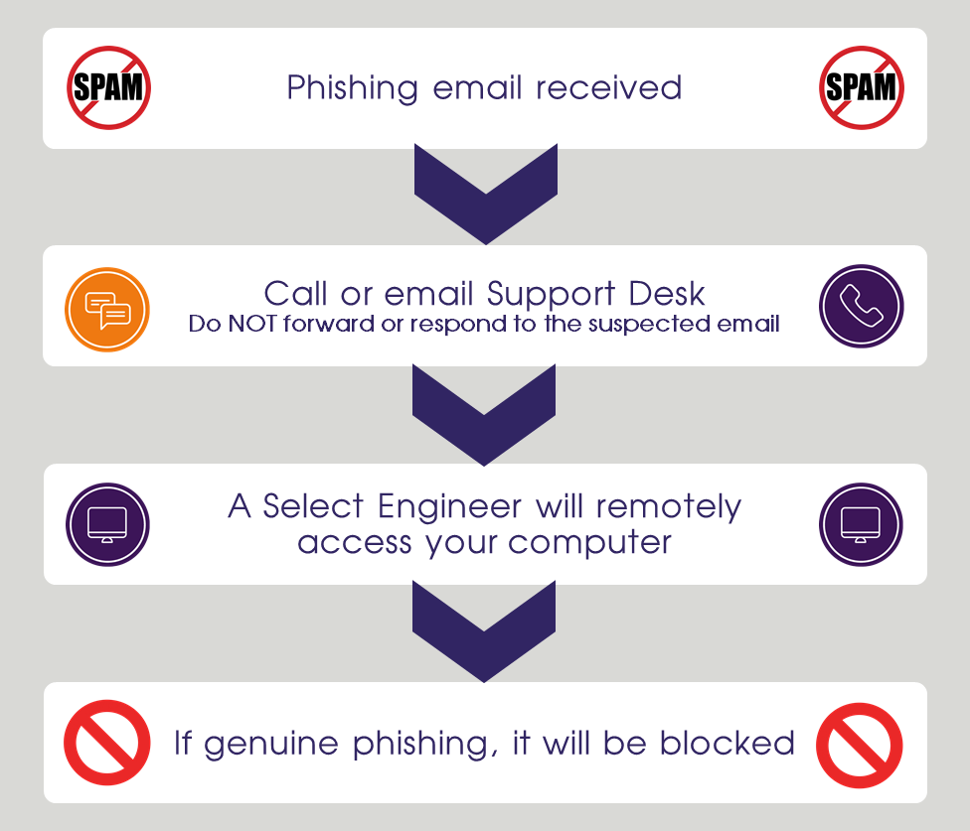
- Firstly, NEVER forward a suspicious email on to someone else, you will most likely be spreading the risk around and increasing the chances that someone follows the scammers actions.
- Contact you IT support via phone or email (a separate email) and ask for help.
The Select Technology process is that we will remote access your computer and interrogate the potential phishing email and determine if it is safe or not. If not, it will be blocked.