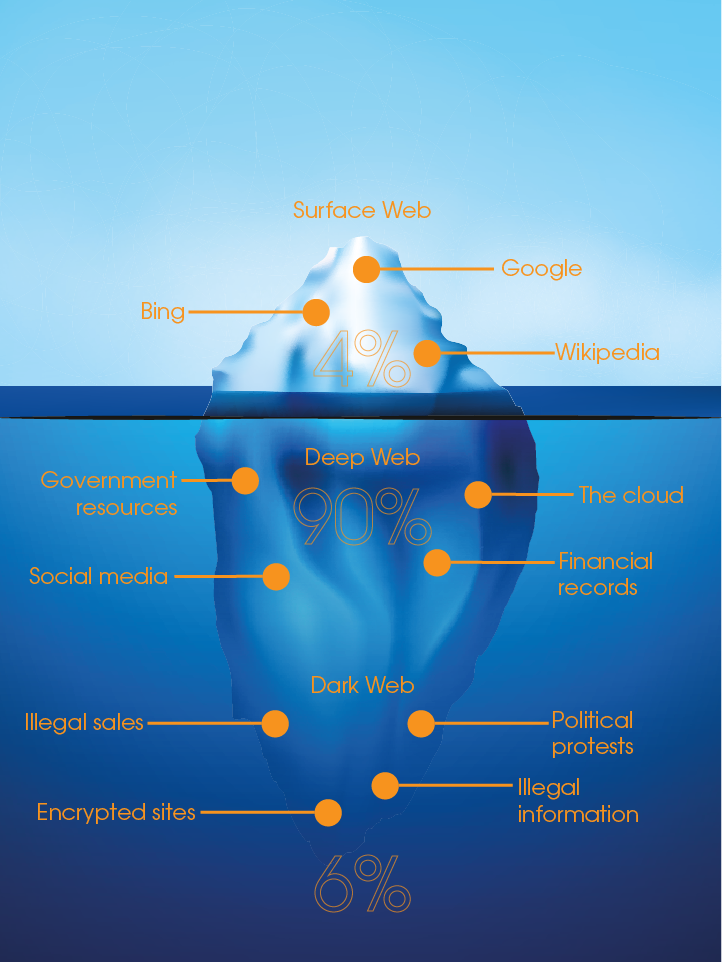
What is the dark web?
The internet is a layered universe, the surface web, the deep web and the dark web. The different layers are based on how you access them. The surface web is accessible via your standard search engines such as Google, Bing etc and would include all your favourite websites. The deep web is content stored by organisations, people and are not accessible via search engines, but via passwords and forms. The dark web is only accessible via specialist browsers, that allow you to access the dark web anonymously, and in this part of the internet, is where you will find illegal activity, including drug trafficking, arm sales and the sale/sharing of stolen information.