How safe are you online? Check out our top tips to make sure you’re Cybersecurity Savvy
Protecting your cybersecurity online
Unfortunately, potential security threats are everywhere, so it’s important for us to be as aware of these as possible. The following advice and tips are by no means exhaustive but provide a great starting point of how to mitigate as many avenues of attack as possible and make life difficult for the bad guys!
Ultimately, threat actors (the tech term for the bad guys) are financially motivated; cybercrime offers a very attractive money-making prospect with minimal risk vs. traditional crime and typically carries more lenient penalties if caught. So, the more difficult you make it for them to get a return, the less of them you have to worry about.
So, what can you do to improve your cybersecurity and avoid online scams?
As individuals we need to focus on sensible and simple security. Making your life too difficult defeats the point of technology and will actively discourage us from being vigilant.
Therefore, following on from our password security tips, we’ve put together a set of simple cybersecurity awareness guidelines that can help you to stay protected in your personal life. Raising awareness of our personal cybersecurity naturally changes our attitudes to security in the workplace, helping businesses to become more secure as a by-product. So, any business owners or team leaders reading this, take note!
4 Top Tips to keep you safe online
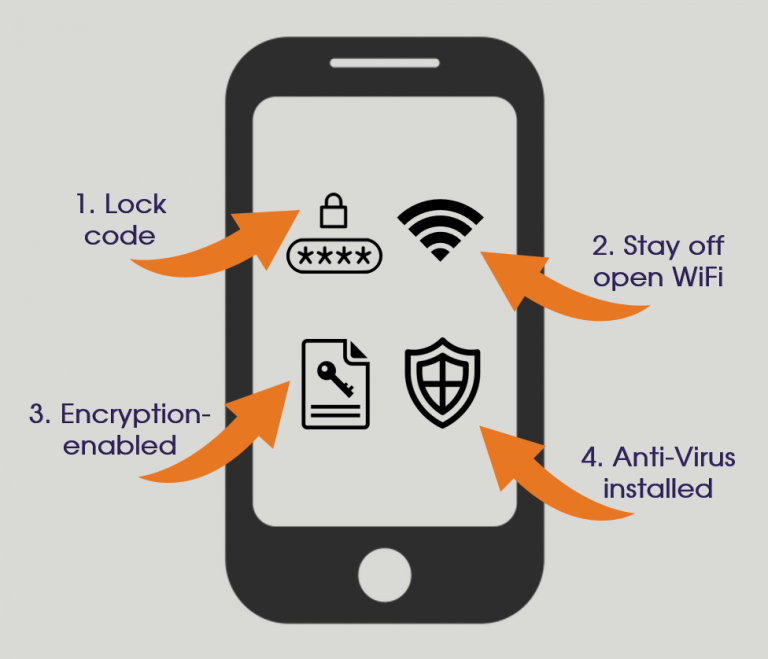
Tip 1: SmartPhone Care
The Risk:
Like it or not, your mobile phone is the Trojan horse in your pocket. We all love our phones and have far more information about ourselves and our lives on them than ever (whether we realise it or not). This means our phones are a great entry point for attackers.
The Solution:
There are several things we can do to help protect our phones and keep our information safe without impacting the way we use them:
- Lock Screen: Make sure your phone has a lock code or lock pattern or some form of bio-metric (face ID, fingerprint reader, etc.) so people can’t just pick up your phone and start going through your e-mails, messages and photos. Bio-metric is the best for convenience as you can effectively unlock your phone with zero effort.
- Encryption: Again, this is something most phones support these days and doesn’t impact the way the phone works as everything is happening behind the scenes; encryption makes the storage on the phone (including any memory cards you’ve installed) un-readable by other devices. if your phone is stolen and the thief can’t get past the lock screen they may hook your phone up to another device to access the storage that way. If you have encryption-enabled your data will be unreadable to them.
- Anti-Virus: Most phones come with a third-party Anti-virus product these days, but if not, go to the App store or Google Play and download something reputable like Avast. Most tend to offer free AV to individual consumers. Make sure you set-up scheduled scans of your phone for when you’re likely to be sleeping so you don’t have the annoyance of your phone running slow when you’re trying to use it!
- WiFi: Data is part of our day-to-day lives, we are consuming more and more internet connectivity than ever before. One thing we’re probably all guilty of is using and abusing any free WiFi we can get our grubby mitts on! Outside the office, every store or coffee shop we visit seems to have free guest WiFi these days, but how trustworthy is this? Believe it or not, it’s fairly common for bad guys to impersonate an outlet’s free WiFi so they can try to capture our traffic to extract passwords and infect our devices. What’s worse is that our phone will automatically betray us: most of us set our phones (and other personal devices) to connect to WiFi networks automatically for convenience, but did you know our devices don’t just connect to networks we’ve used before once they’re in range, they actually broadcast to see if they’re out there. This means all the bad guys need to do is pick up these broadcasts then pretend to be one of those networks. I’ve genuinely seen my device connect to my home WiFi whilst in a coffee shop 40+ miles away; as good as my home WiFi solution is, I don’t believe that was genuine! Therefore, make sure you think twice about using guest WiFi and when you’re not at home or in the office turn your WiFi off to reduce your exposure to this kind of attack.
Tip 2: Phishing
The Risk:
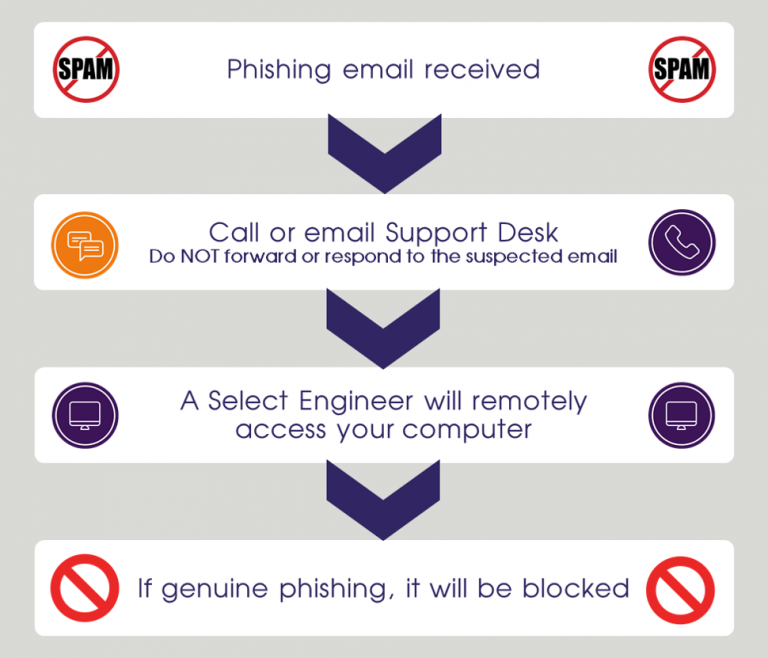
For those that aren’t aware of this term, Phishing is often mixed up with Spam but it actually has a more malicious intent. Phishing emails typically impersonate persons of authority – sometimes internal to a business and sometimes external. Their purpose is to get us as users to do something not in our best interest, such as click a bad link which can infect our machine(s), get us to input our login details to a bogus login page or illicit money from us.
The Solution
The first two approaches – bad links and fake logins – tend to use a shot gun approach in that they are sent out automatically and indiscriminately, waiting for someone to fall victim. They tend to go for things that are ubiquitous to us as people: Facebook logins, fake news articles, missing Amazon deliveries, etc.
To check whether a link is bad, hover your cursor over the link before clicking. This displays the actual address the link is going to and if it’s gibberish or half a page long you know it’s best avoided. That said, some cloud services do have pretty long links so it can be a challenge. The best advice here is to never click on the links, never call the number(s) and definitely never open the attachments. Go to the actual page of the site in a fresh tab and log in; most platforms/services include alerts/messages/order tracking, etc that are pertinent to your account.
Schemes to illicit money from us are much more tailored. Using information gathered about a business or individual via a website or social media, allows the threat actor to create a pretext for their communication making it far less obvious. An example of this is if you are advertising for a vacancy in your team, an attacker may craft an application or enquiry email with a malicious attachment or link. In some instances, the attacker(s) could already be in the system, reviewing channels of communication and chipping in at the last minute, impersonating the more authoritative member to ‘update bank details’ or ‘release funds to’, etc. Protecting against those kinds of sophisticated attacks can be tricky and while there is technology which can help, the most simple and effective method of prevention is simply calling and talking to one another to discount any concerns.
Tip 3: Anti-Social Media
The Risk:
We’re all connected to some form of social media, whether it’s for personal or work purposes and we have all received friend/connection requests from people we don’t know. Social Media now suffers from its own form of Phishing: Threat actors use fake accounts to make contact with people to either spread malicious links via chats (these typically come in the form of “Check out this news article” or “Please take a look at a paper I’m writing/CV” etc), or glean information about us via social engineering; you’d be amazed how much info you give away in your social media profiles and how you actually use this info yourself in your day to day online activities.
The Solution:
Here’s a test for yourself: do you use a significant date(s) or telephone number(s) in any of your passwords, pins or security questions? What about the names of pets and children?
Now, do any of these feature in posts in your profiles (birthdays and anniversaries are the most common)? If the answer to any of these is ‘No’, well done you, but I’m willing to bet there is a significant number of you this does apply to (and there are plenty of industry stats out there to support my cynicism!). Therefore, although it makes me sound pretty grumpy, it really does pay to be anti-social! Quite simply if you get a request or connect suggestion from someone you don’t know or if they just don’t have a profile photo you recognise, don’t accept it. Instead, reach out via other means if this is someone you want to be involved with.

Tip 4: Spam Handling
The Risk:
Spam is something we all suffer from every now and then. It comes from the good old days of leaflets and sales letters which used to come through our front doors. For the most part, Spam tends to be genuine sales noise, but some can be malicious. Typically businesses should have some established mechanism or process, so it is important to understand your Spam handling process. Processes will differ from business to business, but largely they will use one of the following methods:
- Spam management is the responsibility of the user via their Email client: For example, Office 365 Outlook users will be familiar with dropping into their Spam/Junk folder(s) periodically to check for messages and use Outlook to bock senders.
- Separate Spam management: many of you may be familiar with receiving a daily with a summary (digest) of messages that have been blocked. These digest reports give you the ability to release messages via the mail itself or you can sign into a portal to do it; one word of caution I would impart is that once again threat actors are using these digests as a means of phishing you.
The Solution:
There are several things to be mindful of from both a personal and workplace perspective when handling SPAM:
- Use your built in Spam tools: On a domestic level, if you use something like Gmail or Hotmail simply block the sender and send report messages via your mail provider
- One thing that is a definite: don’t use the ‘Unsubscribe’ link as threat actors will often use this as their bad URL to help you infect your machine
- Above all else: DO NOT FORWARD the message, NOT EVEN TO YOUR IT TEAM. At best this would be propagating Spam, at worst you could be spreading the infection. If you need to report it, take a screen shot and pass that on to IT
- Be familiar with your Spam handling process; if your company doesn’t use a digest system and no ones told you they’re introducing one, just delete it and contact IT
- Open a fresh tab to your Spam portal and login to take a look
To sum up…
Improve your cybersecurity and ensure you’re security savvy by following these tips:
- Do a 4-point check on your Smart Phone to make sure you’re as protected as possible
- Be vigilant when you receive emails, particularly those with suspect URLs, attachments or phone numbers
- Pick up the phone! Double check things with your colleagues if something isn’t adding up
- Be anti-social and reject any friend requests you’re not 100% sure about
- If in doubt, report, but NEVER forward or respond to an email you suspect is malicious spam or phishing
- Overall, be mindful. By educating yourself, you are more likely not to fall into the traps of the bad guys!
If you want to find out more about cybersecurity, online scams, spam and phishing and how it can be avoided, contact us
